Cybersecurity researchers have discovered an updated version of a backdoor called INFORMATION ON THE AWARD which is distributed via spear-phishing attacks.
The findings come from Japanese firm ITOCHU Cyber & Intelligence, which said the malware “has been updated with new features, as well as changes to anti-analysis (analysis evasion) techniques.”
LODEINFO (versions 0.6.6 and 0.6.7) was first documented by Kaspersky in November 2022, detailing its capabilities to execute arbitrary shellcode, take screenshots, and exfiltrate files on an actor-controlled server.
A month later, ESET revealed attacks against Japanese political institutions that led to the deployment of LODEINFO.

The backdoor is the work of a Chinese nation-state actor known as Stone Panda (also known as APT10, Bronze Riverside, Cicada, Earth Tengshe, MirrorFace, and Potassium), which has a history of orchestrating attacks against Japan since 2021.
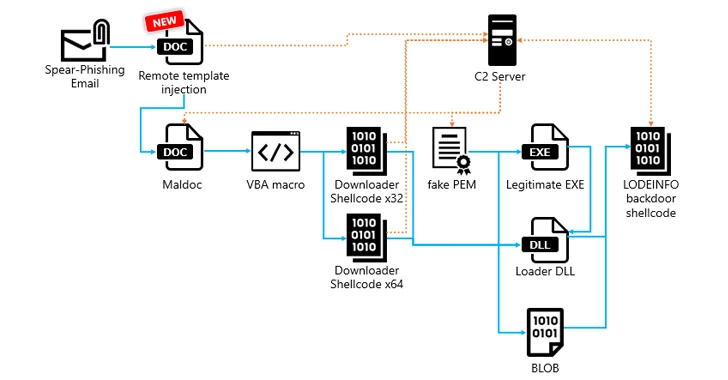
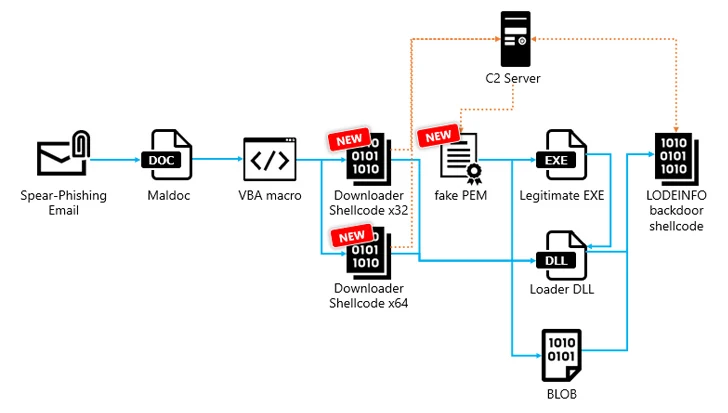
Attack chains begin with phishing emails containing malicious Microsoft Word documents that, when opened, execute VBA macros to launch downloader shell code that can ultimately execute the LODEINFO implant.
LODEINFO infection routes have also been observed in 2023 that use remote template injection methods to retrieve and execute malicious macros hosted on the adversary’s infrastructure whenever the victim opens a decoy Word document containing the template.
Additionally, checks to check Microsoft Office’s language settings to determine whether it is Japanese were said to have been added around June 2023, only to be removed a month later in attacks leveraging LODEINFO version 0.7.1.

“Also, the name of the maldoc file itself has been changed from Japanese to English,” ITOCHU noted. “From this, we believe that version 0.7.1 was likely used to attack environments in languages other than Japanese.”
Another notable change in attacks delivering LODEINFO version 0.7.1 is the introduction of a new intermediate step that involves the shellcode downloader retrieving a file masquerading as Privacy-Enhanced Mail (PEM) from a C2 server, which, in its time, load the backdoor directly into memory.

The downloader shares similarities with a well-known fileless downloader named DOWNIISSA based on the self-patching mechanism to hide malicious code, the encoding method for command and control (C2) server information, and the structure of the data decrypted from the fake file PEM.
“LODEINFO backdoor shellcode is fileless malware that allows attackers to remotely access and manage infected hosts,” the company said, with samples found in 2023 and 2024 incorporating additional commands. The latest version of LODEINFO is 0.7.3.
“As a countermeasure, since both the downloader shellcode and LODEINFO backdoor shellcode are fileless malware, it is essential to introduce a product that can scan and detect malware in memory to detect it,” he added.