
Cybersecurity researchers have uncovered a targeted operation against Ukraine that exploited a nearly seven-year-old flaw in Microsoft Office to deliver Cobalt Strike on compromised systems.
The attack chain, which occurred in late 2023 according to Deep Instinct, uses as its starting point a PowerPoint presentation file (“signal-2023-12-20-160512.ppsx”), the name of which implies that it may have been shared via the Signal instant messaging app.
That said, there is no concrete evidence to suggest that the PPSX file was distributed in this way, although the Computer Emergency Response Team of Ukraine (CERT-UA) discovered two different campaigns that used the messaging app as a vehicle of vector malware in the past.
Just last week, the agency revealed that the Ukrainian military is increasingly being targeted by the UAC-0184 group via messaging and dating platforms to serve malware such as HijackLoader (also known as GHOSTPULSE and SHADOWLADDER), XWorm, and Remcos RAT , as well as open source malware programs such as sigtop and tusc to exfiltrate data from computers.

“The PPSX file (PowerPoint presentation) appears to be an old US Army instruction manual for mine clearing blades (MCB) for tanks,” security researcher Ivan Kosarev said. “The PPSX file includes a remote relationship with an external OLE object.”
This involves exploitation of CVE-2017-8570 (CVSS score: 7.8), a now fixed remote code execution bug in Office that could allow an attacker to perform arbitrary actions after convincing a victim to open a file specially designed to load a remote script hosted on weavesilk[.]space.
The heavily obfuscated script subsequently launches an HTML file containing JavaScript code, which, in turn, sets persistence on the host via the Windows registry and drops a next-stage payload that impersonates the Cisco AnyConnect VPN client.
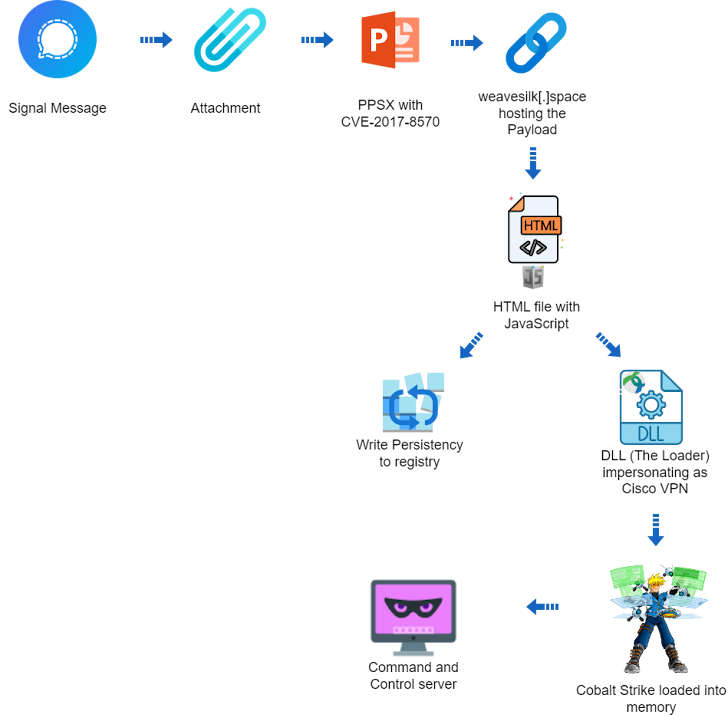
The payload includes a dynamic link library (DLL) that ultimately injects a cracked Cobalt Strike Beacon, a legitimate pen-testing tool, directly into the system’s memory and awaits further instructions from a command and control (C2) server ( “petapixel[.]fun”).
The DLL also packs functionality to check whether it is running in a virtual machine and evade detection by security software.
Deep Instinct said it could neither link the attacks to a specific threat actor or group nor rule out the possibility of a red teaming operation. The exact end goal of the intrusion is also unclear.

“The bait contained military content, suggesting it was targeting military personnel,” Kosarev said.
“But domain names spin silk[.]space and petapixels[.]fun are disguised as an obscure generative art site (weavesilk[.]com) and a popular photography site (petapixel[.]com). These are unrelated, and it is a bit baffling why an attacker would use them specifically to deceive military personnel.”
The disclosure comes as CERT-UA revealed that around 20 energy, water and heating suppliers in Ukraine were targeted by a Russian state-sponsored group called UAC-0133, a sub-cluster within Sandworm (aka APT44, FROZENBARENTS, Seashell Blizzard, UAC-0002 and Voodoo Bear), responsible for a large part of all destructive and destructive operations against the country.
The attacks, which aimed to sabotage critical operations, involve the use of malware such as Kapeka (aka ICYWELL, KnuckleTouch, QUEUESEED and wrongsens) and its Linux variant BIASBOAT, as well as GOSSIPFLOW and LOADGRIP.
While GOSSIPFLOW is a Golang-based SOCKS5 proxy, LOADGRIP is an ELF binary written in C used to load BIASBOAT on compromised Linux hosts.
Sandworm is a prolific and highly adaptive threat group linked to Unit 74455 within the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU). It is known to have been active since at least 2009, with the adversary also linked to three hack-and-leak hacktivist figures such as XakNet Team, CyberArmyofRussia_Reborn, and Solntsepek.
“Sponsored by Russian military intelligence, APT44 is a dynamic and operationally mature threat actor, actively engaged in the full spectrum of espionage, attack and influence operations,” Mandiant said, describing the Advanced Persistent Threat (APT) as engaged in a multi-intensive effort to help Russia gain a wartime advantage from January 2022.
“APT44’s operations are global in scope and reflect Russia’s wide-ranging national interests and ambitions. Patterns of activity over time indicate that APT44 is tasked with a number of different strategic priorities and is most likely viewed by the Kremlin as a flexible power tool capable of serving both enduring and emerging intelligence requirements.”