
A new ongoing malware campaign has been observed distributing three different thieves, such as CryptBot, LummaC2, and Rhadamanthys hosted on CDN (Content Delivery Network) cache domains since at least February 2024.
Cisco Talos attributed the activity with moderate confidence to a threat actor tracked as CoralRaider, a purported group of Vietnamese origin that came to light earlier this month.
This assessment is based on “several overlaps of tactics, techniques and procedures (TTPs) from CoralRaider’s Rotbot campaign, including the initial attack vector of the Windows Shortcut file, the intermediate PowerShell decryptor and payload download scripts, the FoDHelper technique used to bypass the User Access Controls (UAC) of the victim machine,” the company said.

The campaign objectives span various business verticals across multiple geographies, including the United States, Nigeria, Pakistan, Ecuador, Germany, Egypt, United Kingdom, Poland, Philippines, Norway, Japan, Syria and Turkey.
The attack chains involve users downloading files disguised as movie files via a web browser, increasing the possibility of a large-scale attack.
“This threat actor is using a Content Delivery Network (CDN) cache to store malicious files on its network edge host in this campaign, avoiding request delays,” said Talos researchers Joey Chen, Chetan Raghuprasad, and Alex Karkins . “The actor uses the CDN cache as a download server to deceive network defenders.”
The initial entry vector for drive-by downloads is suspected to be phishing emails, used as a conduit to propagate explosive links pointing to ZIP archives containing a Windows shortcut (LNK) file.
The link file, in turn, executes a PowerShell script to retrieve a next-stage HTML application (HTA) payload hosted in the CDN cache, which then executes Javascript code to launch an embedded PowerShell loader that takes the necessary steps to fly under the radar and ultimately download and execute one of three stealer malware.

The PowerShell modular loader script is designed to bypass user access controls (UAC) on the victim’s computer using a known technique called FodHelper, which has also been used by Vietnamese threat actors linked to another thief known as NodeStealer capable to steal Facebook account data.
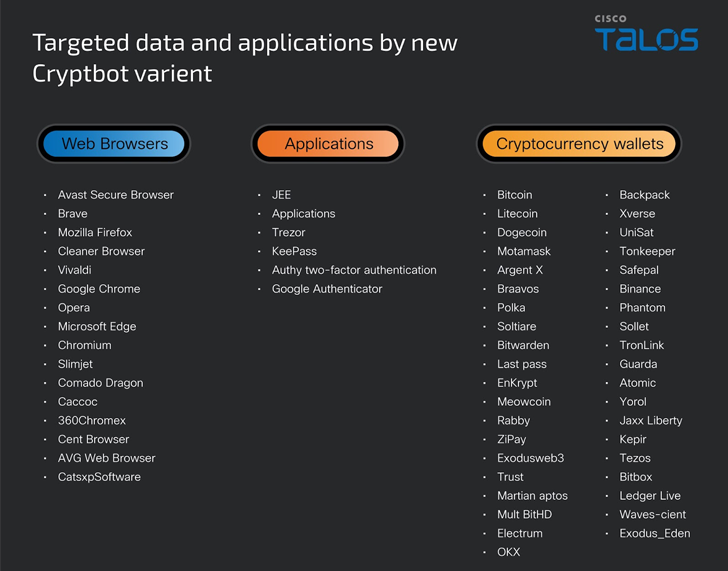
Thieving malware, regardless of what it is distributed, captures victims’ information, such as system and browser data, credentials, cryptocurrency wallets, and financial information.
What is noteworthy about the campaign is that it uses an updated version of CryptBot that packs new anti-analysis techniques and also captures password management application databases and authentication application information.