
With many of 2023’s highly publicized cyber attacks revolving around one or more SaaS applications, SaaS has become a real concern in many boardroom discussions. More than ever, considering that GenAI applications are, in fact, SaaS applications.
Wing Security (Wing), a SaaS security company, conducted an analysis of 493 companies using SaaS in the fourth quarter of 2023. Their study reveals this the way businesses use SaaS today and the wide variety of threats that arise from that use. This unique analysis provides rare and important insights into the breadth and depth of SaaS-related risks, but also provides practical suggestions for mitigating them and ensuring that SaaS can be widely used without compromising the security posture.
The TL;DR version of SaaS security
2023 has brought some now infamous examples of malicious players exploiting or directly targeting SaaS, including North Korean group UNC4899, ransomware group 0ktapus, and Russian Midnight Blizzard APT, which have targeted well-known organizations such as JumpCloud, MGM Resorts and Microsoft (respectively), and probably many others that often pass without notice.
The first insight from this research solidifies the concept that SaaS is the new supply chain, providing an almost intuitive picture of the importance of ensuring the use of SaaS. These applications are clearly an integral part of the modern organization’s set of tools and vendors. That said, long gone are the days when every third party with access to company data had to undergo security audits or IT approval. Even in the most rigorous companies, when a diligent employee needs a quick and efficient solution, he will seek it out and use it to do his job faster and better. Again, think about the widespread use of GenAI and the picture is clear.
Therefore, any organization concerned about the security of its supply chain must adopt SaaS security measures. According to the MITER ATT&CK “Trust Relationships” technique (T1199), a supply chain attack occurs when an attacker targets a supplier to exploit it as a means to infiltrate a larger network of companies. By entrusting sensitive data to external SaaS providers, organizations expose themselves to supply chain risks that go beyond immediate security concerns.
Four common SaaS risks
There are various reasons and ways SaaS is being targeted. The good news is that most risks can be significantly mitigated if monitored and controlled. Basic SaaS security features they are even freesuitable for organizations that are just starting to develop their SaaS security strategy or need to benchmark it against their current solution.
1) Shadow SaaS
The first problem with using SaaS is the fact that it often goes completely unnoticed: the number of applications used by organizations is typically 250% greater than a basic and often used query of the workspace reveals.
Among the companies analyzed:
- 41% of applications were used by just one person, resulting in a very long queue of unauthorized applications.
- 1 in 5 users were using applications not used by anyone else in their organization, creating security and resource issues.
- 63% of single-user applications were not accessible even within a 3-month period, raising the question: why keep them connected to company data?
- 96.7% of organizations have had at least one application that had a security incident in the previous year, solidifying ongoing risk and the need for adequate mitigation.
2) Bypass the AMF
Wing’s research points to a trend where users are choosing to use a username/password to access the services they need, bypassing security measures in place (see image 1).
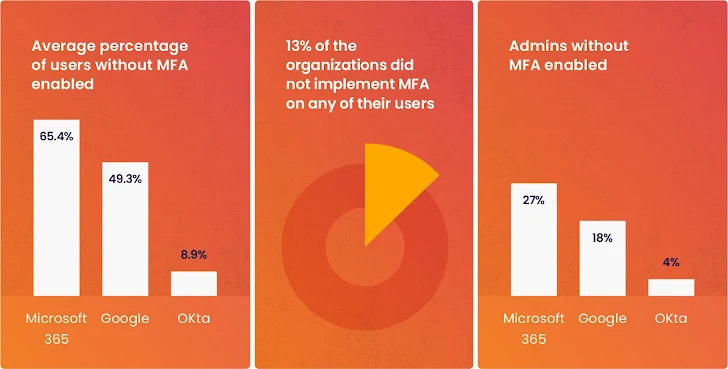 |
| Image 1: From Wing Security’s research, bypassing MFA. |
3) Forgotten tokens
Users grant tokens to the applications they need; this is necessary for SaaS applications to serve their purpose. The problem is that these tokens are often forgotten after a few or just one use. Wing’s research revealed a large presence of unused tokens over a 3-month period, creating an unnecessarily large attack surface for many customers (Image 2).
4) The new risk of shadow AI
At the beginning of 2023, security teams have mainly focused on a few well-known and selected services that offer access to AI-based models. However, as the year progressed, thousands of conventional SaaS applications adopted AI models. Research shows that 99.7% of businesses use applications with built-in AI capabilities.
Organizations had to agree to updated terms and conditions that allowed these applications to use and refine their models using the organizations’ most sensitive data. Often, these revised terms and conditions have gone unnoticed, along with the use of AI itself.
There are several ways that AI applications can use your data for their training models. This can come in the form of learning from your data, storing your data, and even needing a human to manually review your data to improve the AI model. According to Ala, this ability is often configurable and entirely avoidableas long as it is not overlooked.
Solving SaaS security challenges in 2024
The report ends on a positive note, listing 8 ways companies can mitigate the growing SaaS supply chain threat. Included:
- Continuous identification and management of shadow IT.
- Prioritize fixing SaaS misconfigurations
- Optimize anomaly detection with pre-built frameworks, automate when possible.
- Discover and monitor all SaaS applications that use AI, and constantly monitor your SaaS for updates in the terms and conditions related to the use of AI.
For the full list of findings, tips on ensuring safe SaaS usage, and SaaS security predictions for 2024, download the full report here.