
Cybersecurity researchers have detected another variant of the Phobos ransomware family known as Faust.
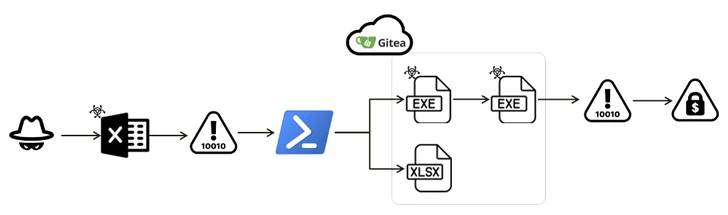
Fortinet FortiGuard Labs, which detailed the latest iteration of the ransomware, said it is propagating via an infection that delivers a Microsoft Excel (.XLAM) document containing a VBA script.
“The attackers used the Gitea service to store several Base64-encoded files, each containing malicious binary code,” security researcher Cara Lin said in a technical report published last week. “When these files are placed into a system’s memory, they initiate a file encryption attack.”
Faust is the latest addition to several ransomware variants in the Phobos family, including Eking, Eight, Elbie, Devos, and 8Base. It is worth noting that Faust was previously documented by Cisco Talos in November 2023.
The cybersecurity firm described the variant as active from 2022 and “does not target specific sectors or regions.”

The attack chain begins with an XLAM document that, when opened, downloads Base64-encoded data from Gitea to save a harmless XLSX file, while surreptitiously fetching an executable masquerading as an updater for the AVG AntiVirus software (” AVG updater. exe”).
The binary, for its part, works as a downloader to fetch and launch another executable named “SmartScreen Defender Windows.exe” in order to initiate the encryption process by employing a fileless attack to distribute the malicious shellcode.
“The Faust variant shows the ability to maintain persistence in an environment and creates multiple threads for efficient execution,” Lin said.
The development comes as new ransomware families such as Albabat (aka White Bat), DHC, Frivinho, Kasseika, Kuiper, Mimus, NONAME and NOOSE have gained traction, with the former a Rust-based malware distributed in the form of fraudulent software as a fake Windows 10 digital activation tool and a cheat program for the Counter-Strike 2 game.
Trellix, which examined the Windows, Linux and macOS versions of Kuiper earlier this month, attributed the Golang-based ransomware to a threat actor called RobinHood, who first publicized it on underground forums in September 2023 .
“The concurrency-focused nature of Golang benefits the threat actor by avoiding race conditions and other common issues when dealing with multiple threads, which otherwise would have been a (near) certainty,” the security researcher said Max Kersten.
“Another factor exploited by the Kuiper ransomware, which is also a reason for the growing popularity of Golang, is the language’s cross-platform capabilities to create builds for a variety of platforms. This flexibility allows attackers to adapt their code with little effort, especially because the majority of the code base (i.e. cryptography related activity) is pure Golang and does not require rewriting for a different platform.”
NONAME is also notable for the fact that its data leak site mimics that of the LockBit group, raising the possibility that it may be another LockBit or compiling leaked databases shared by LockBit on the official leak portal, researcher Rakesh Krishnan he underlined.
The findings follow a report from French cybersecurity firm Intrinsec linking the nascent 3AM (also spelled ThreeAM) ransomware to the Royal/BlackSuit ransomware, which, in turn, emerged following the shutdown of cybercrime syndicate Conti in May 2022.

The links arise from a “significant overlap” in tactics and communication channels between the 3 AM ransomware and “the shared infrastructure of the former Conti-Ryuk-TrickBot nexus.”
It’s not all. Ransomware authors have been observed once again using TeamViewer as an initial entry vector to breach target environments and attempt to deploy ciphers based on the LockBit ransomware builder, leaked in September 2022.
“Threat actors seek any available means of access to individual endpoints to wreak havoc and possibly extend their reach further into the infrastructure,” cybersecurity firm Huntress said.
According to the AhnLab Security Intelligence Center (ASEC), LockBit 3.0 has also been distributed in the form of Microsoft Word files disguised as resumes in recent weeks targeting entities in South Korea.
Despite the amorphous and ever-evolving nature of the ransomware ecosystem, there are signs that victims are increasingly refusing to pay, causing the percentage of ransomware victims who chose to pay to drop to 29% in Q4 2023, down from 41% in the third quarter. and 34% in the second quarter. A previous low of 28% was recorded in the third quarter of 2022.
The average ransom payment for the time period dropped 33%, from $850,700 to $568,705, according to data shared by ransomware trading firm Coveware. The average ransom payment, however, remained unchanged at $200,000, compared to $190,424 in the second quarter of 2023.
“The industry continues to get smarter about what can and cannot reasonably be obtained by paying a ransom,” the company said. “This has led to better assistance for victims and lower payments for non-material insurance.”