The North Korea-linked state actor known as Kimsuky is suspected of using a previously undocumented Golang-based information thief called Troll thief.
The malware steals “SSH, FileZilla, C drive files/directories, browser, system information, [and] screens” from infected systems, South Korean cybersecurity firm S2W said in a new technical report.
Troll Stealer’s links to Kimsuky stem from its similarities to known malware families, such as the AppleSeed and AlphaSeed malware that have been attributed to the group.

Kimsuky, also tracked under the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (formerly Thallium), Nickel Kimball, and Velvet Chollima, is well known for his propensity to steal sensitive and classified information in offensive cyber operations.
In late November 2023, the threat actors were sanctioned by the US Treasury Department’s Office of Foreign Assets Control (OFAC) for gathering information to further North Korea’s strategic objectives.
The adversary collective has, in recent months, been attributed to spear-phishing attacks that targeted South Korean entities to deliver a variety of backdoors, including AppleSeed and AlphaSeed.
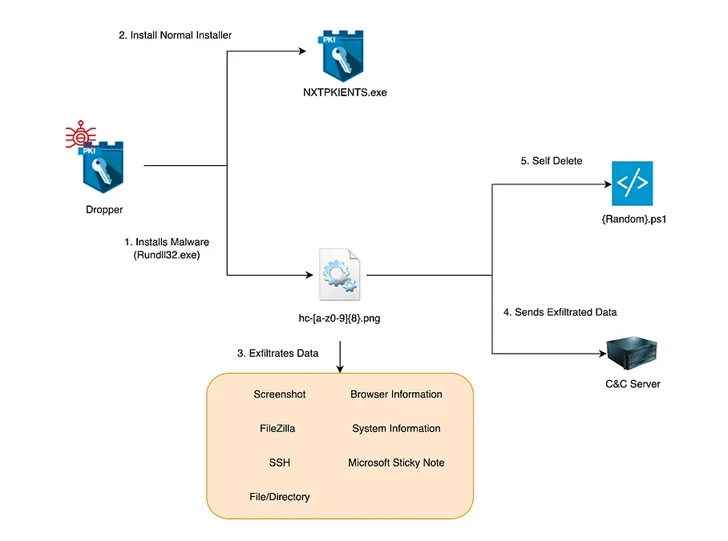
S2W’s latest analysis reveals the use of a dropper masquerading as a security program installation file from a South Korean company called SGA Solutions to launch the stealer, which takes its name from the path “D:/~/repo/golang /src/root .go/s/troll/agent” embedded within it.
“The dropper functions as a legitimate installer alongside the malware, and both the dropper and the malware are signed with a valid and legitimate D2Innovation Co.,LTD certificate, suggesting that the company’s certificate was indeed stolen,” the company said. society.
A distinguishing feature of Troll Stealer is its ability to steal the GPKI folder on infected systems, raising the possibility that the malware was used in attacks against administrative and public organizations in the country.

Given the absence of Kimsuky campaigns documenting the theft of GPKI folders, the possibility has been raised that the new behavior is a change in tactics or the work of another threat actor closely associated with the group who also has access to the source code of AppleSeed. and AlphaSeed.
There are also signs that the threat actor may be involved with a Go-based backdoor called GoBear, which is also signed with a legitimate certificate associated with D2Innovation Co., LTD and executes instructions received from a command and control server (C2 ).
“The strings contained in the names of the invoked functions were found to overlap with commands used by BetaSeed, a C++-based backdoor malware used by the Kimsuky group,” S2W said. “Interestingly, GoBear adds SOCKS5 proxy functionality, which was previously not supported by the Kimsuky group’s backdoor malware.”