
Indian government bodies and energy companies have been targeted by unknown threat actors with the aim of delivering a modified version of an open source information-stealing malware called HackBrowserData and exfiltrating sensitive information in some cases using Slack as command and control (C2) .
“The information thief was delivered via a phishing email, disguised as an invitation letter from the Indian Air Force,” EclecticIQ researcher Arda Büyükkaya said in a report published today.
“The attacker used Slack channels as exfiltration points to upload confidential internal documents, private email messages, and cached web browser data after the malware was executed.”
The campaign, observed by the Dutch cybersecurity firm starting March 7, 2024, was codenamed Operation FlightNight in reference to the Slack channels operated by the adversary.

The targets of the malicious activity span multiple government entities in India, including those related to electronic communications, IT governance, and national defense.
The threat actor is said to have successfully compromised private energy companies, collecting financial documents, personal details of employees, details of oil and gas drilling activities. In total, approximately 8.81 GB of data was stolen during the campaign.
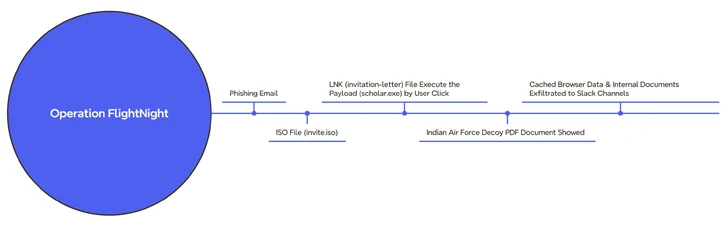
The attack chain begins with a phishing message containing an ISO file (“invite.iso”), which in turn contains a Windows shortcut (LNK) that triggers the execution of a hidden binary file (“scholar.exe”) present within the image file of the mounted optical disc.
At the same time, a decoy PDF file purporting to be an invitation letter from the Indian Air Force is displayed to the victim while the malware clandestinely collects documents and data cached in the web browser and transmits them to a Slack channel controlled by the actor called FlightNight.
The malware is a modified version of HackBrowserData that goes beyond the browser’s data-stealing capabilities to incorporate features to steal documents (Microsoft Office, PDF, and SQL database files), communicate on Slack, and better evade detection using obfuscation techniques.

The threat actor is suspected to have stolen the bait PDF during a previous intrusion, with behavioral similarities traced back to a phishing campaign targeting the Indian Air Force with a Go-based thief called GoStealer.
The details of the activity were disclosed by an Indian security researcher known by the pseudonym xelemental (@ElementalX2) in mid-January 2024.
GoStealer’s infection sequence is virtually identical to FlightNight’s, using procurement-themed decoys (“SU-30 Aircraft Procurement.iso”) to display a decoy file while the thief’s payload is deployed to exfiltrate information of interest on Slack.
By adapting freely available offensive tools and repurposing legitimate infrastructure such as Slack, prevalent in enterprise environments, it allows threat actors to reduce development time and costs, as well as easily go undetected.
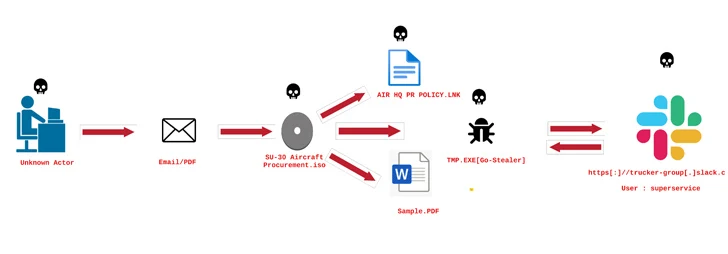 |
| Image Source: ElementalX2 |
The efficiency benefits also mean that it is much easier to launch a targeted attack, allowing even the least skilled and aspiring cybercriminals to spring into action and inflict significant damage on organizations.
“Operation FlightNight and the GoStealer campaign highlight a simple but effective approach by threat actors in using open source tools for cyber espionage,” Büyükkaya said.
“This highlights the evolving cyber threat landscape, where actors are abusing widely used open source offensive tools and platforms to achieve their goals with minimal risk of detection and investment.”