COMMENT
2024 is shaping up to be a landscape of unprecedented volatility in cybersecurity. With regulatory changes, third-party service incidents and economic uncertainties looming, the need for board involvement in risk management programs is critical.
It also has dollars attached. Data breaches are two to three times more costly for organizations where boards are not actively involved in cyber discussions. There is also a growing demand for CISOs to find innovative ways to communicate their company’s risk environment to stakeholders.
Additionally, regulators are imposing new fiduciary requirements. For example, the U.S. Securities and Exchange Commission’s cyber regulations require disclosure of “material” cyber incidents within four days of determining the materiality of an event, in an effort to align boards of directors with this growing cyber threat. The rulings also require annual disclosure of material risks and how the company manages them.
CISOs use agreed-upon materiality definitions to communicate risk to executives and boards. This helps them clarify what materiality means for their particular organization and assess the likelihood of cyber incidents. But for many CISOs, materiality remains an ambiguous term, open to interpretation based on an organization’s unique cybersecurity environment.
Determination of material loss with industry benchmarks
The crux of the confusion over materiality is determining what constitutes a “material loss.” It’s a challenging, but essential, discussion to have. The most explicit industry definition published so far – by Dr. Jack Freund, Kovrr’s chief risk officer and Distinguished ISSA Fellow, and Natalie Jorion, who formulated the Freund-Jorion cyber materiality heuristic – rates materiality at 0, 01% of prior year revenue, equal to approximately one basis point of revenue. (As we’ll see below, this equates to about an hour of revenue for Fortune 1000 companies.)
By testing different thresholds against industry benchmarks, organizations can gain a clearer understanding of their vulnerability to material cyber attacks. Kovrr recently modeled predicted cyber incidents experienced by US Fortune 1000 companies. Each organization was analyzed based on a customized collection of events and responses from security controls, producing a Cyber Risk Quantification (CRQ) assessment that revealed the probability and cost of each event by sector.
THE “Fortune 1000 Cyber Risk Report” estimates the probability of a Fortune 1000 company experiencing cyber losses totaling more than a threshold. For example, the model estimates the probability of suffering cyber losses totaling $50 million, which is approximately $1.2 days of revenue. While significant, this can be considered substantially low: a $100 million incident equates to 2.4 days of revenue, while a $500 million incident represents nearly two weeks of operations – undoubtedly a material loss for the average Fortune 1000 company.
To put these numbers into context, the average annual revenue of a Fortune 1000 company is approximately $15 billion, and daily revenue is approximately $41 million. This is a more practical interpretation of the model results, which can support financial planning.
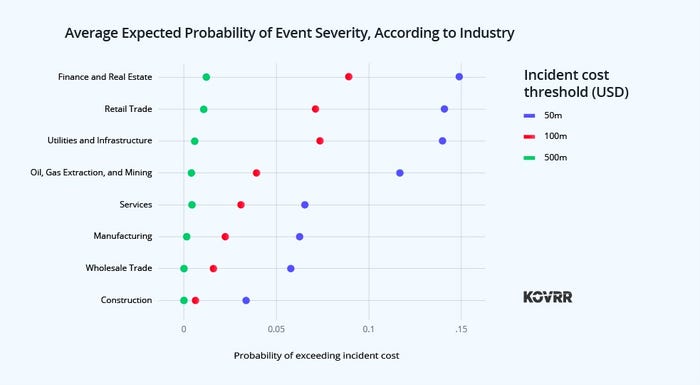 Average expected probability of the severity of the event. Source: Fortune 1000 Cyber Risk Report (Peter Dyson, Kovrr, November 2023)
Average expected probability of the severity of the event. Source: Fortune 1000 Cyber Risk Report (Peter Dyson, Kovrr, November 2023)The chart above illustrates the likelihood of organizations in a specific industry experiencing a loss based on magnitude, which can result from a single significant event or a series of smaller incidents that indicate weaknesses in an organization’s cybersecurity strategy .
Specifically, the financial and real estate, retail, utilities, oil and gas extraction, and mining industries all have a greater than 10% (1 in 10) chance of cyber events costing their companies more than $50 million (within 12 months). and a greater than 5% (1 in 20) chance of costing more than $100 million.
While a one in 10 chance of experiencing an event that costs an organization a day of revenue seems like a high probability, if the incident were reduced to an hour, the probability would be much higher.
Define materiality to protect against material events
CISOs can use a variety of strategies to determine materiality thresholds, allowing them to make necessary investments in the areas of the business most subject to material risks. With precise definitions, executives and cybersecurity leaders can collaborate and make data-driven decisions that accurately reflect an organization’s threat landscape.
First, CISOs should identify which triggering events are most likely to result in a material loss in their industry. While there are general trends, including the high cost of data breaches, a more in-depth evaluation is needed. For example, the chart below, showing the average (most probable) cost of events by type, reveals that extortion and service provider events present a higher risk for many organizations.
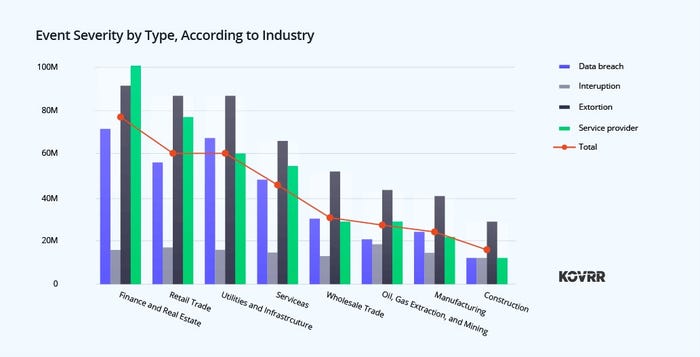 Event severity by type. Source: Fortune 1000 Cyber Risk Report (Peter Dyson, Kovrr, November 2023)
Event severity by type. Source: Fortune 1000 Cyber Risk Report (Peter Dyson, Kovrr, November 2023)Through the financial insights provided by a CRQ solution, CISOs can effectively communicate to the board the benefits of improving security controls, attitudes and practices, demonstrating the potential reduction in the likelihood of material events and overall costs .
Finally, it is critical to monitor organizational risk on an ongoing basis. The external threat environment and the costs of remediation are subject to regular changes.
While 2024 is set to be one of the busiest years for cybersecurity staff, implementing a data-driven framework that clearly defines material losses can facilitate more direct discussions with the board and foster a culture of resilience informatics.