
Threat actors are exploiting a recently disclosed security flaw affecting Ivanti Connect Secure, Policy Secure, and ZTA gateways to implement a code-named backdoor DSLog on sensitive devices.
This is according to the findings of Orange Cyberdefense, which said it observed the exploitation of CVE-2024-21893 within hours of the public release of the proof-of-concept (PoC) code.
CVE-2024-21893, disclosed by Ivanti late last month along with CVE-2024-21888, relates to a server-side request forgery (SSRF) vulnerability in the SAML module which, if successfully exploited, could allow access to otherwise limited resources without any authentication.
The Utah-based company has since acknowledged that the flaw limited targeted attacks, although the exact scope of the compromises is unclear.

Then, last week, the Shadowserver Foundation revealed an increase in exploitation attempts targeting the vulnerability originating from over 170 unique IP addresses, shortly after both Rapid7 and AssetNote shared additional technical specifications.
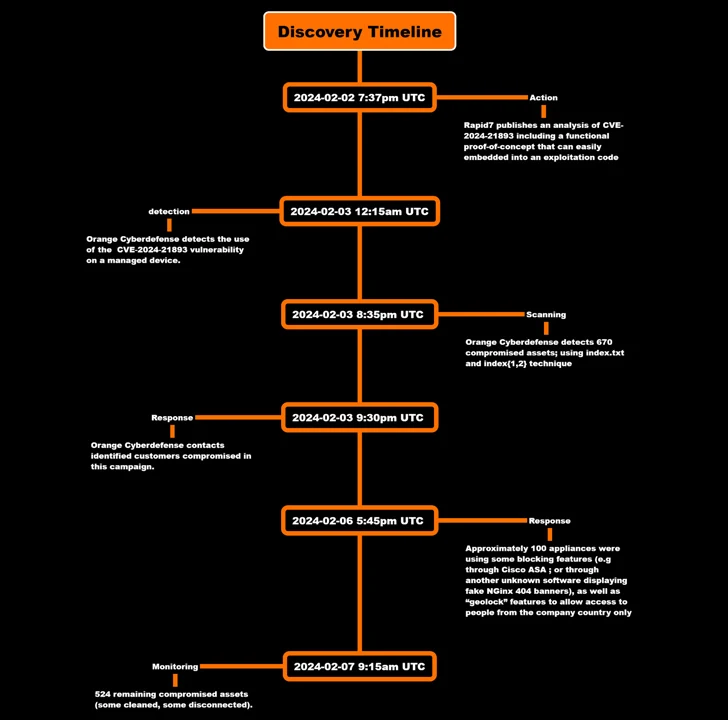
The latest analysis from Orange Cyberdefense shows that compromises were detected as early as February 3, with the attack targeting an unnamed client to inject a backdoor that grants persistent remote access.
“The backdoor is inserted into an existing Perl file called ‘DSLog.pm,’” the company said, highlighting an ongoing pattern in which existing legitimate components – in this case, a logging module – are modified to add the malicious code.
DSLog, the implant, comes with its own tricks to hinder analysis and detection, including embedding a unique hash for each device, thus making it impossible to use the hash to contact the same backdoor on another device .
The same hash value is provided by attackers to the User-Agent header field in an HTTP request to the appliance to allow the malware to extract the command to execute from a query parameter called “cdi”. The decoded instruction is then executed as the root user.
“The web shell does not return status/code when you try to contact it,” Orange Cyberdefense said. “There is no known way to detect it directly.”

It also observed evidence of threat actors deleting “.access” logs on “multiple” devices in an attempt to hide the forensic trail and fly under the radar.
But by checking artifacts created during the triggering of the SSRF vulnerability, the company said it was able to detect 670 compromised assets during an initial scan on February 3, a number that dropped to 524 as of February 7.
In light of the continued exploitation of Ivanti devices, “all customers are strongly advised to factory reset their device before applying the patch to prevent the threat actor from gaining update persistence in their environment.”