The technology, research and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part of a recent wave of cyberattacks.
The intrusions pave the way for an updated version of the modular backdoor called Waterbear, as well as its enhanced successor called Deuterbear.
“Waterbear is known for its complexity, using a variety of evasion mechanisms to minimize the possibility of detection and analysis,” Trend Micro researchers Cyris Tseng and Pierre Lee said in an analysis last week.
“In 2022, Earth Hundun started using the latest version of Waterbear, also known as Deuterbear, which features several changes, including anti-memory scanning and decryption routines, which make us consider it a different malware entity from the original Waterbear.”

The cybersecurity firm is tracking the threat actor under the nickname Earth Hundun, known to be active since at least 2007. It also goes by other names such as Circuit Panda, HUAPI, Manga Taurus, Palmerworm, Red Djinn, and Temp.Overboard . .
In a joint advisory published last September, the cybersecurity and intelligence agencies of Japan and the United States attributed the adversary to China, describing its ability to modify router firmware and exploit domain trust relationships router to move from international branches to their corporate headquarters based in the two countries.
“BlackTech actors use customized malware, dual-use tools, and above-ground living tactics, such as disabling access on routers, to hide their operations,” the governments said.

“After gaining an initial foothold in a target network and gaining administrator access to the network’s edge devices, BlackTech cyber actors often modify the firmware to hide their activity across the edge devices to further maintain persistence in the network.”
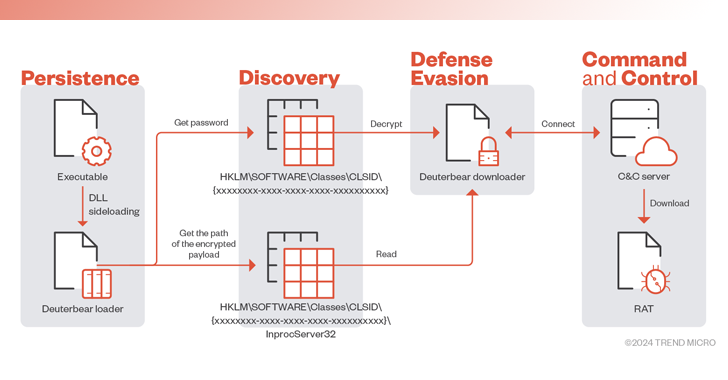
One of the crucial tools in its multi-faceted arsenal is Waterbear (also known as DBGPRINT), which has been in use since 2009 and has been constantly updated over the years with improved defense evasion capabilities.
The remote access trojan core is retrieved from a command and control (C2) server via a downloader, which is launched using a loader which, in turn, is executed via a known technique called DLL sideloading.
The latest version of the plant supports nearly 50 commands, allowing it to perform a wide range of tasks, including process enumeration and termination, file operations, window management, startup, and exit from the remote shell, taking screenshots, and editing the Windows registry, among others.

Since 2022, Deuterbear is also used using a similar infection flow, whose downloader implements a number of obfuscation methods to resist anti-analysis and uses HTTPS for C2 communications.
“Since 2009, Earth Hundun has continuously evolved and refined the Waterbear backdoor, as well as its many variants and offshoots,” the researchers said.
“The Deuterbear downloader uses HTTPS encryption to protect network traffic and implements various updates in malware execution, such as altering the decryption function, checking debuggers or sandboxes, and modifying traffic protocols.”