
New cybersecurity research has found that Amazon Web Services (AWS) and Google Cloud command-line interface (CLI) tools can expose sensitive credentials in build logs, posing significant risks to organizations.
The vulnerability has been given a code name Leaky CLI from cloud security company Orca.
“Some commands on the Azure CLI, AWS CLI, and Google Cloud CLI can expose sensitive information in the form of environment variables, which can be collected by adversaries when published by tools like GitHub Actions,” security researcher Roi Nisimi said in a report shared with The Hacker News.
Microsoft has since addressed the issue as part of security updates released in November 2023, assigning it the identifier CVE-2023-36052 (CVSS score: 8.6).

The idea, in a nutshell, has to do with how CLI commands could be used to show (pre)defined environment variables and send output to continuous integration and continuous deployment (CI/CD) logs . A list of such commands spanning AWS and Google Cloud is less than 0
- get-aws lambda-function-configuration
- aws lambda get function
- configuration-function-update-aws lambda
- aws lambda-update-function-code
- aws lambda publish version
- gcloud functions distribute
–set-env-vars - gcloud functions distribute
–update-env-vars - gcloud functions distribute
–remove-env-vars
Orca said it found several projects on GitHub that inadvertently leaked access tokens and other sensitive data via Github Actions, CircleCI, TravisCI, and Cloud Build logs.

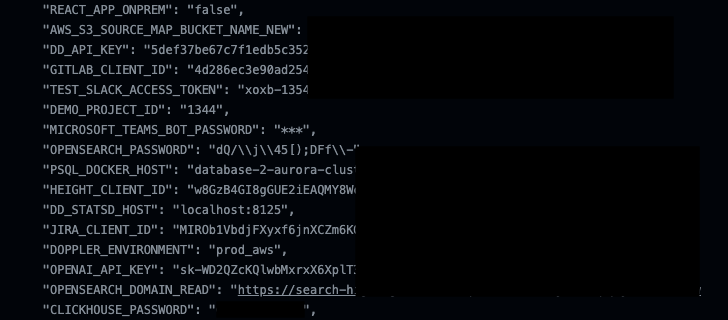
Unlike Microsoft, however, both Amazon and Google consider this to be expected behavior, requiring that organizations take steps to avoid storing secrets in environment variables and instead use a dedicated secrets storage service such as AWS Secrets Manager or Google Cloud Secret Manager.

Google also recommends using the “–no-user-output-enabled” option to suppress printing command output to standard output and standard error in the terminal.
“If attackers get their hands on these environment variables, it could potentially lead to them viewing sensitive information including credentials, such as passwords, usernames, and keys, which could allow them to access any resources accessible to the repository owners,” Nisimi said. .
“CLI commands are assumed by default to run in a secure environment, but together with CI/CD pipelines they could pose a security threat.”